- Scans the entire network, recognizes all equipment and shows present vulnarabilities.
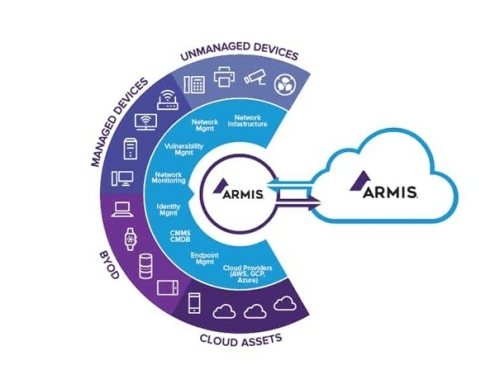
- Agentless protection of all (un)managed assets (IT/OT/IoT/IoMT), including equipment on which EDR cannot be installed.
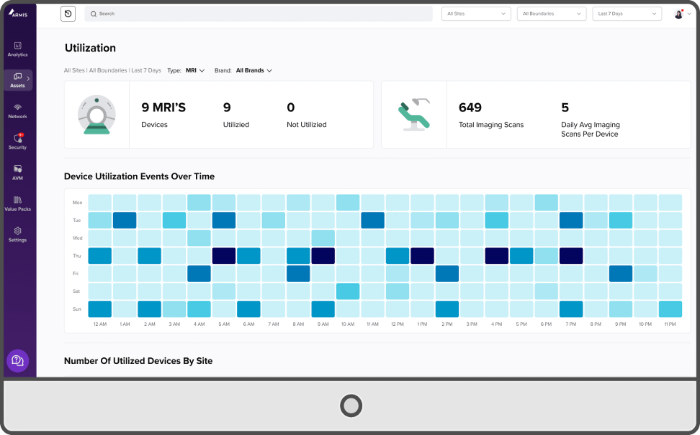
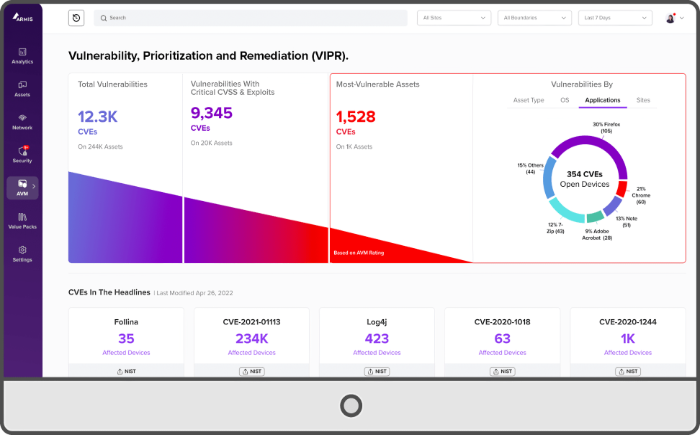
- Real-time insight into vulnerabilities of all devices connected to your network, what to do to protect you and in what order actions should be taken.
- Asset-, vulnerability- and threat-intelligence is combined by Armis using its cloud-based, AI-driven Intelligence Engine.
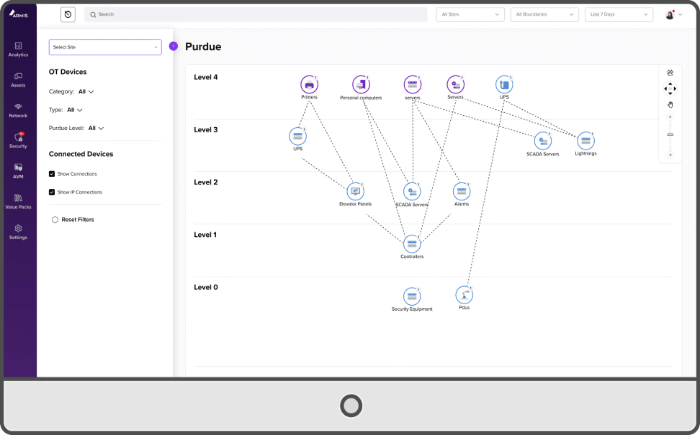
- Every device and every connection always in view with the option to enrich your CMDB.
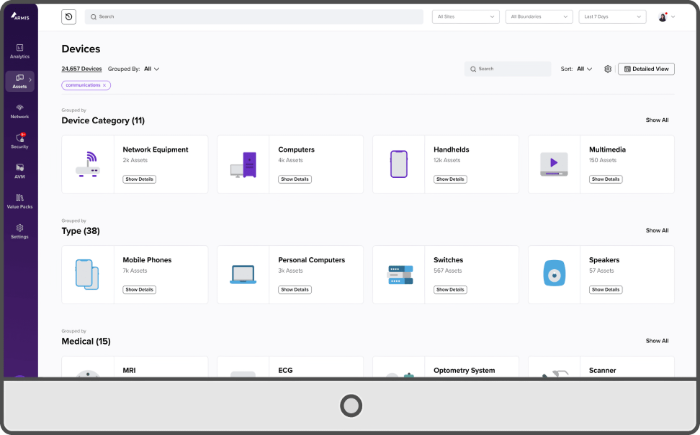
- All findings and warnings visible in a clear dashboard.
- Studies and compares behaviour and intervenes when necessary.
Cyber Security for IT, OT, IoT and IoMT -
Managed and unmanaged
Cyber Security for IT, OT, IoT and IoMT -
Managed and unmanaged
Armis - IT Security from floor to cloud
To what extent is your complex IT environment susceptible to cyber attacks? Do you know exactly and in real-time what is active in the network and what is happening?
Armis offers you a detailed picture and it proactively helps protect you against cyber attacks. You will have real-time insight into the security risks of your entire IT network, of all systems active within your network and what measures need to be taken.
All (legacy) equipment that is connected to the network in your organization can be a risk, even those that are not immediately linked to IT Security. Such as (older) production equipment, IoT devices and medical equipment. Hackers are looking for access to your IT and sensitive data everywhere. Unfortunately, we see this every day in the news reports.
Secure your managed and unmanaged devices with Armis.
Armis sees and analyzes in real-time every device that connects to your network, including equipment that often fall outside the usual scope. This is not just about a subset of products, but every device you can think of. IT equipment, OT equipment, wired, wireless, managed, unmanaged, all traffic can be evaluated.
Vulnerabilities within your entire ICT-network are then simply presented in a clear overview. You will always have direct insight into where your priorities lie!
Armis controls the available security tooling like a director. It integrates with an extensive list of existing security solutions. After detecting an acute threat, Armis can, for example, automatically instruct your firewall or NAC to block an IP address or port. This enables optimal use of existing investments.
Armis Centrix™ – the entire attack surface defended and managed in real-time, from floor to cloud.
Prevention and remediation
- Proactive through scanning
- Real-time protection
Prioritization of (preventive) actions that need to be carried out, such as:
- Firewall software patching
- Firmware update
Agentless protection:
IT, OT, IoT and IoMT
Compliancy:
- CIS Critical Security Controls
- DORA
- MITRE ATT&CK for ICS
- NIS2
- NIST
- SOCI
- Zero Trust
Armis Centrix testimonial
Armis Centrix testimonial
Proactively limit cyber security risks?
Proactively limit cyber security risks?
SEE